The FBI first identified Ranzy Locker ransomware in late 2020 when the variant began to target victims in the United States. Unknown cyber criminals using Ranzy Locker ransomware had compromised more than 30 US businesses as of July 2021. The victims include the construction subsector of the critical manufacturing sector, the academia subsector of the government facilities sector, the information technology sector, and the transportation sector.
A majority of victims reported the actors conducted a brute force attack targeting Remote Desktop Protocol (RDP) credentials to gain access to the victims’ networks. Recent victims reported the actors leveraged known Microsoft Exchange Server vulnerabilities and phishing as the means of compromising their networks. The actors attempted to locate important files to exfiltrate, such as customer information, PII related files, and financial records. Ranzy Locker is deployed to encrypt files on compromised Windows host systems (including servers and virtual machines) and attached network shares. The Ranzy Locker executable leaves a ransom note in all directories where encryption occurred demanding the victim pay a ransom in exchange for a decryption tool. In an example of double extortion techniques, Ranzy actors in some cases have demanded a second ransom from the victim in exchange for not leaking the data on the Internet.
Technical Details and Indicators
The FBI identified the following indicators of compromise (IOCs) that we assess are likely associated with Ranzy Locker activity.
New User Accounts
The Ranzy Locker actors may establish new accounts on domain controllers, servers, workstations, or the active directories. Newly created accounts with the name “felix” have been observed on at least three victims of the ransomware.
Ransom Note
The ransom note for Ranzy Locker has similarities to the wording in both the AKO and ThunderX ransom notes (Around October 2020 both AKO and ThunderX rebranded themselves as Ranzy Locker Ransomware). An example of the notes is below:
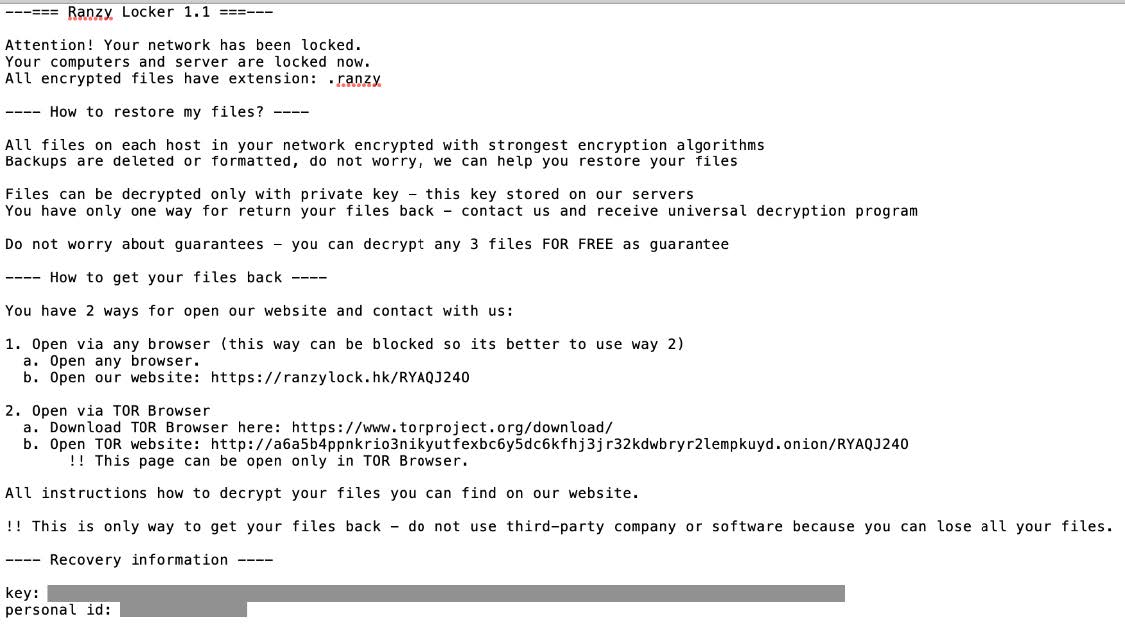 The key found in the ransom note is a base64 encoded string, which when decoded reads:{“ext”:”.ranzy”,”network”:”true/false”,”subID”:”####”,”lang”:”xx-XX.”}
The key found in the ransom note is a base64 encoded string, which when decoded reads:{“ext”:”.ranzy”,”network”:”true/false”,”subID”:”####”,”lang”:”xx-XX.”}
The .ext extension parameter is typically .ranzy for Ranzy Locker 1.1, and the network parameter is typically set to true. The lang parameter is the language of the computer, such as “en-US.”
The subID parameter is an integer and is the name of the Ranzy Locker executable on the system. For example, if the subid is 0000, then the Ranzy Locker executable’s name is 0000.exe.
Ransomware Executable
The name of the Ranzy Locker executable is the subID found in the key on the ransom note. It is a 32-bit portable executable (PE), and all samples observed on different victims have different hash values but identical functionality. The executable requires administrator credentials to run.
Each Ranzy Locker executable contains the same hex encoded strings. Some of these strings are commands used to delete any backups on the system. The table below has the hex string, decoded string, and explanation of the string (if known):
| Hex Strings | Decoded Strings | Explanation |
| 476C6F62616C5C33353335354641352D303745392D343238422D423541352D314338384341423242343838 | Global\35355FA5-07E9-428B-B5A5-1C88CAB2B488 | GUID/UUID |
| 726561646D652E747874 | readme.txt | Ransom note name |
| 776D69632E65786520534841444F57434F5059202F6E6F696E746572616374697665 | wmic.exe SHADOWCOPY /nointeractive | Disables shadow copy notification |
| 776261646D696E2044454C4554452053595354454D53544154454241434B5550 | wbadmin DELETE SYSTEMSTATEBACKUP | Deletes system state backups |
| 776261646D696E2044454C4554452053595354454D53544154454241434B5550202D64656C6574654F6C64657374 | wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest | Deletes oldest system state backup |
| 626364656469742E657865202F736574207B64656661756C747D207265636F76657279656E61626C6564204E6F | bcdedit.exe /set {default} recoveryenabled No | Disables auto startup repair |
| 626364656469742E657865202F736574207B64656661756C747D20626F6F74737461747573706F6C6963792069676E6F7265616C6C6661696C75726573 | bcdedit.exe /set {default} bootstatuspolicyignoreallfailures | Disables Windows Error Recovery |
| 76737361646D696E2E6578652044656C65746520536861646F7773202F416C6C202F5175696574 | vssadmin.exe Delete Shadows /All /Quiet | Deletes all Volume Shadow Copies
|
| 433A5C50726F6772616D2046696C65735C4D6963726F736F66742053514C20536572766572 | C:\Program Files\Microsoft SQL Server
|
SQL server path
|
| 433A5C50726F6772616D2046696C65732028783836295C4D6963726F736F66742053514C20536572766572 | C:\Program Files (x86)\Microsoft SQL Server
|
SQL server path
|
| 534F4654574152455C4D6963726F736F66745C45524944 | SOFTWARE\Microsoft\ERID
|
Registry key |
| 4944 | ID | |
| 7B5041545445524E5F49447D
|
{PATTERN_ID} | |
| 7B4558547D
|
{EXT} | |
| 7B4558547D
|
{UID} | |
| 22657874223A22
|
“ext”:” | Ransom note key parameter
|
| 22657874223A22
|
“key”:”
|
Ransom note key
|
| 226E6574776F726B223A22
|
“network”:”
|
Ransom note key parameter
|
| 227375626964223A22
|
“subid”:”
|
Ransom note key parameter
|
| 226C616E67223A22
|
“lang”:”
|
Ransom note key parameter
|
As these hex strings are present in all Ranzy Locker samples, they provide points for detection such as with YARA. A sample YARA rule can be found here: https://www.tutorialjinni.com/ranzy-ransomware-sample-download.html
In addition to encrypting files and deleting all backups found on the computer, the Ranzy Locker executable attempts to move laterally to other machines on the same network.
Recommended Mitigations:
- Implement regular backups of all data to be stored as air gapped, password protected copies offline. Ensure these copies are not accessible for modification or deletion from any system where the original data resides.
- Implement network segmentation, such that all machines on your network are not accessible from every other machine.
- Install and regularly update antivirus software on all hosts, and enable real time detection.
- Install updates/patch operating systems, software, and firmware as soon as updates/patches are released.
- Review domain controllers, servers, workstations, and active directories for new or unrecognized user accounts.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind. Do not give all users administrative privileges.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs for any unusual activity.
- Consider adding an email banner to emails received from outside your organization.
- Disable hyperlinks in received emails.
- Use double authentication when logging into accounts or services.
